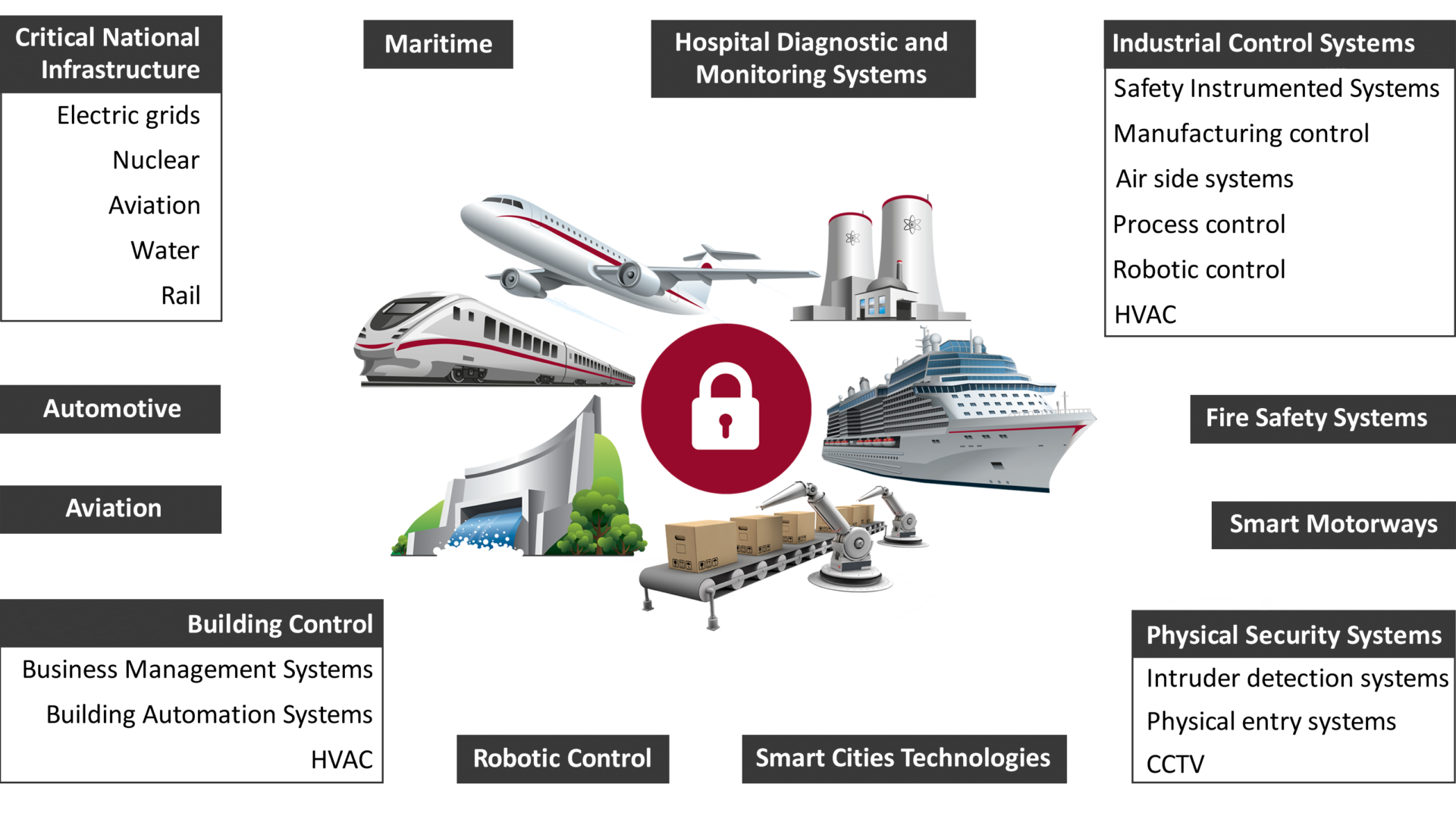
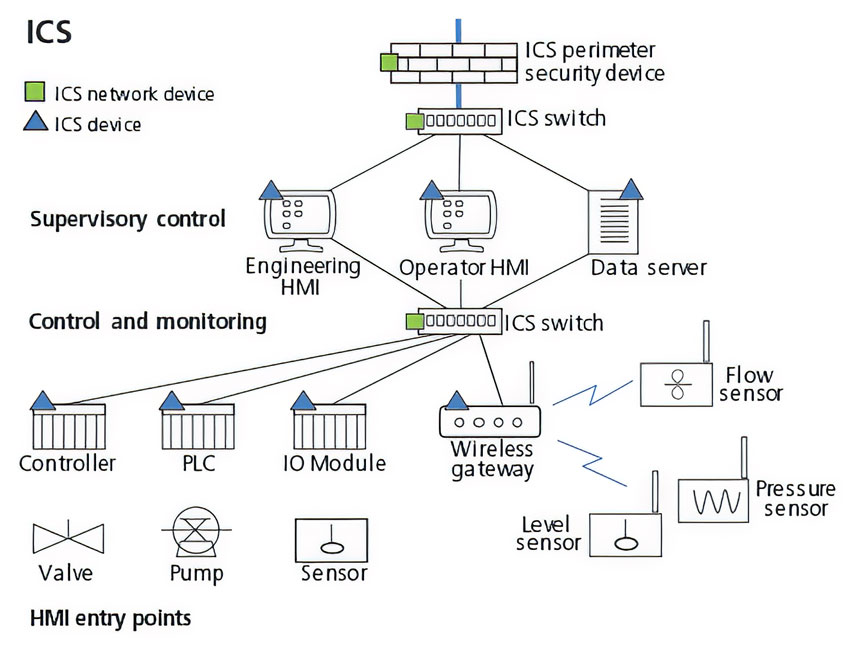
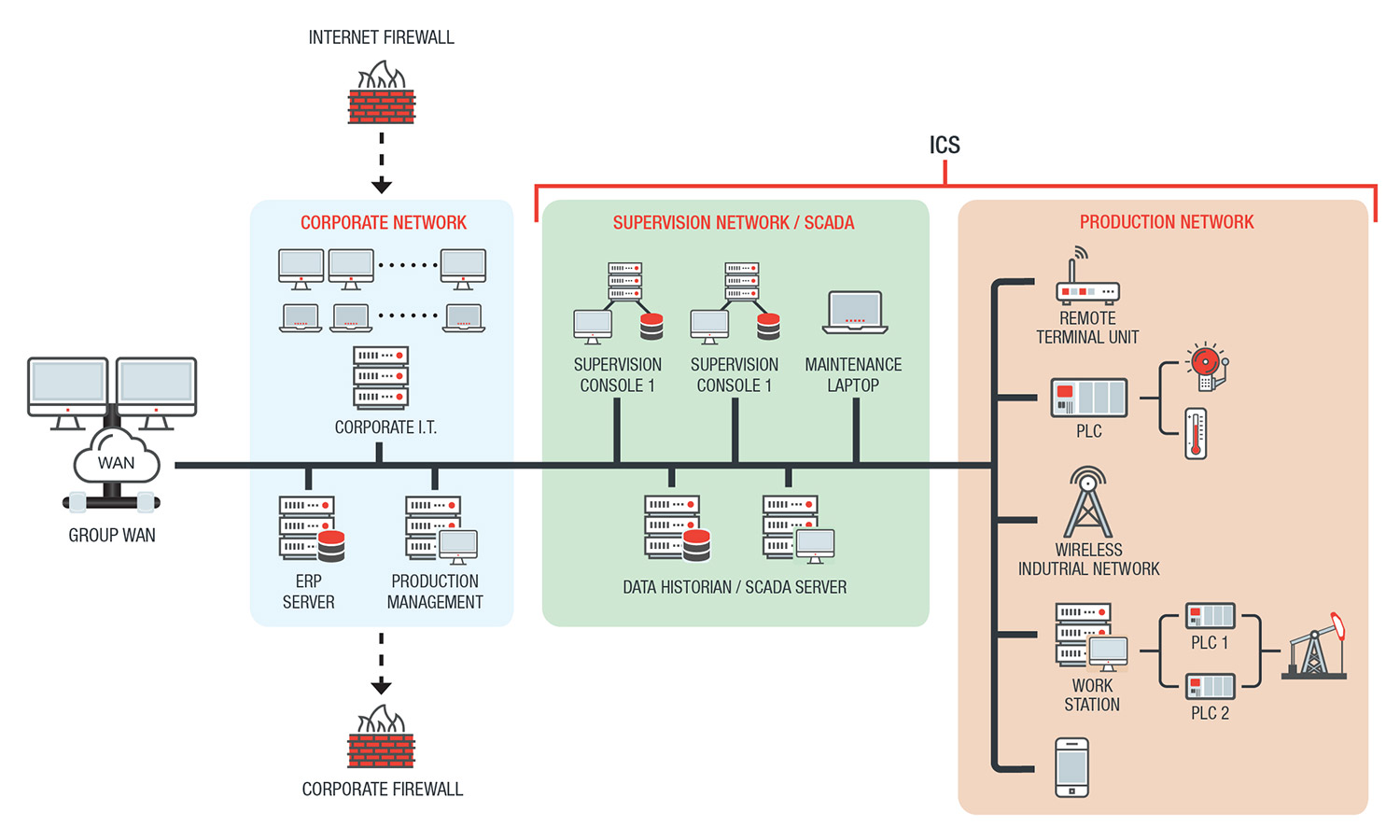
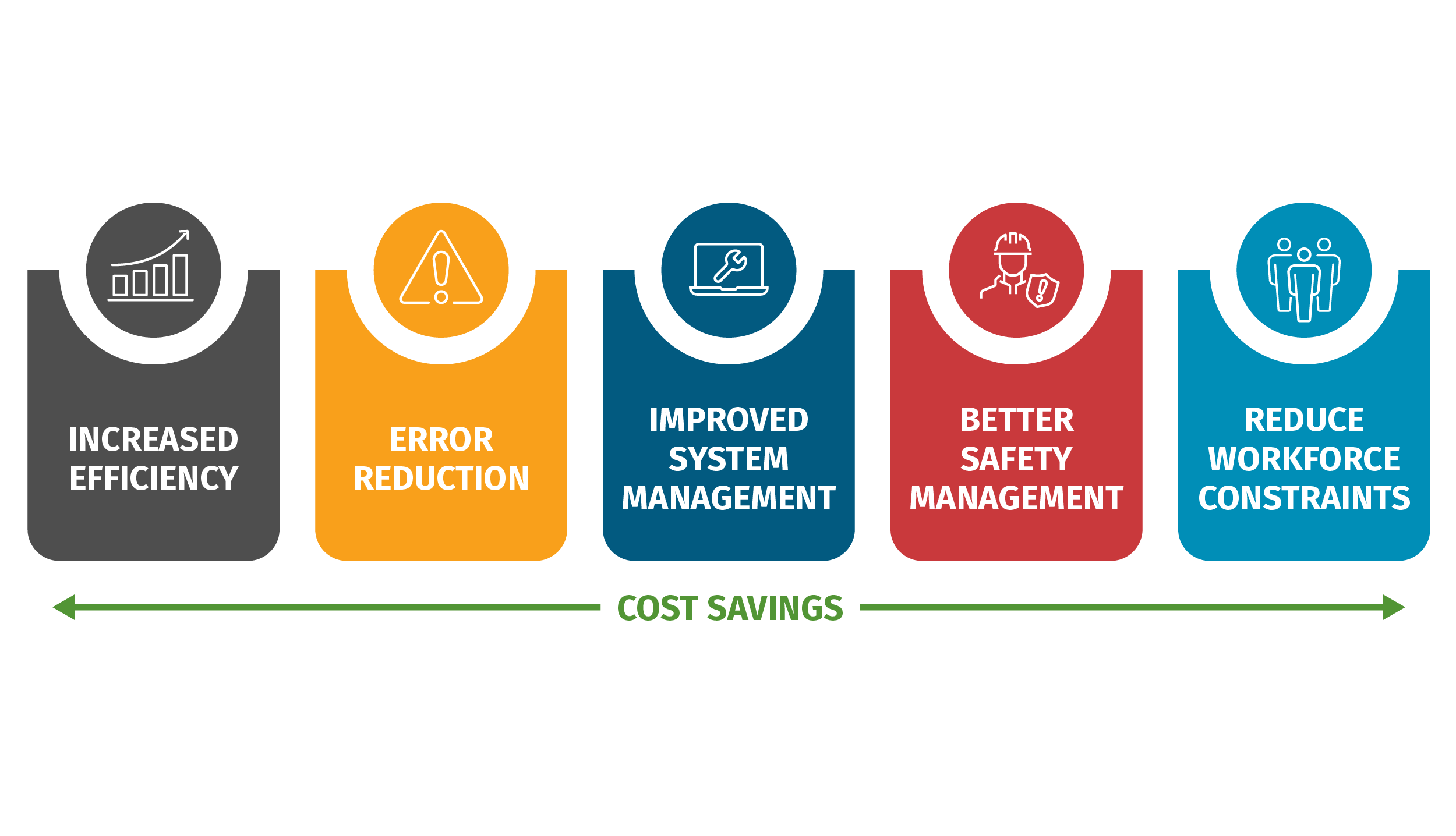
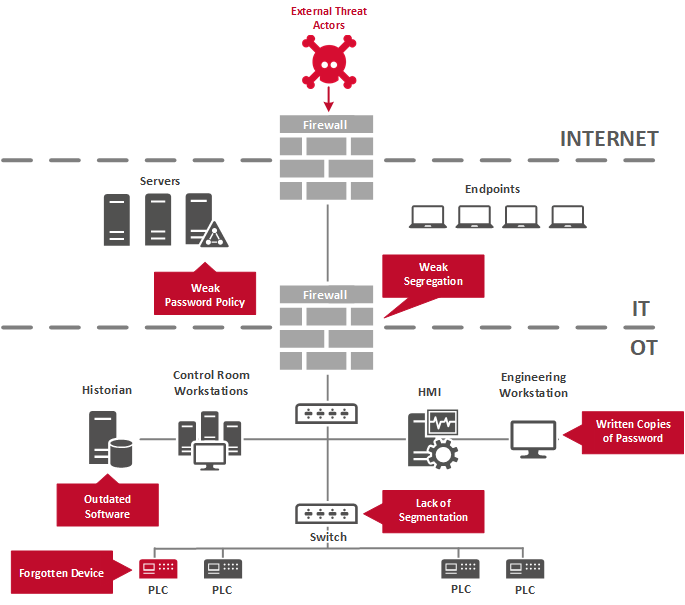
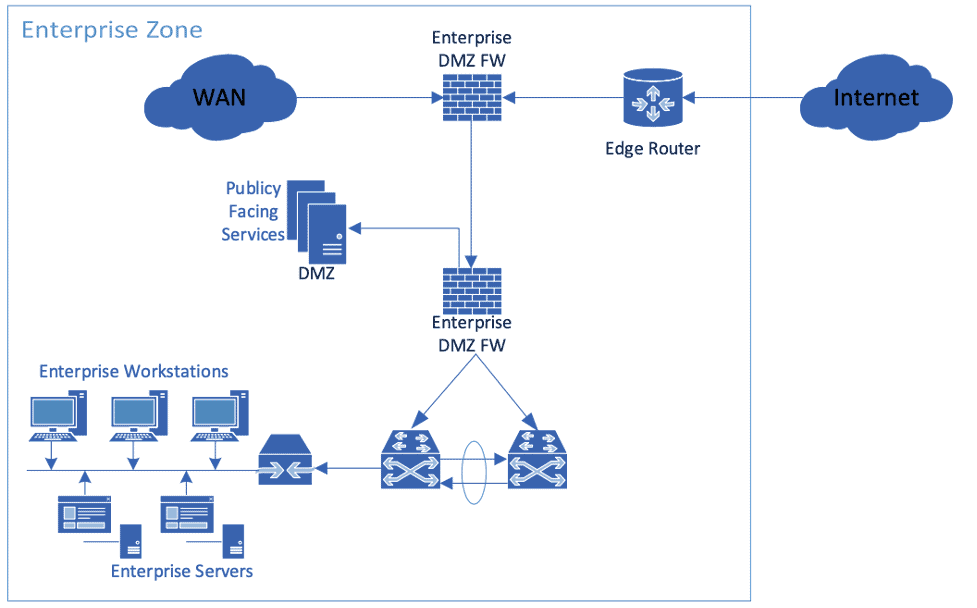
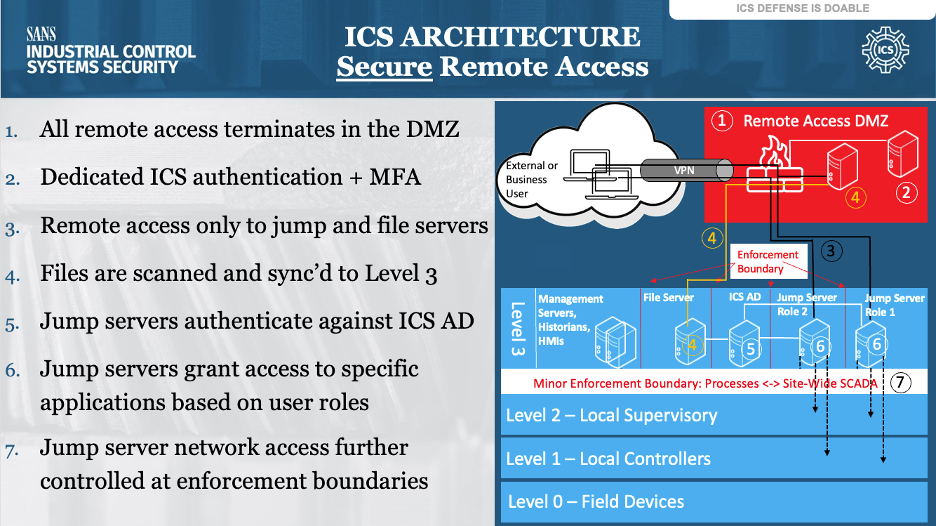
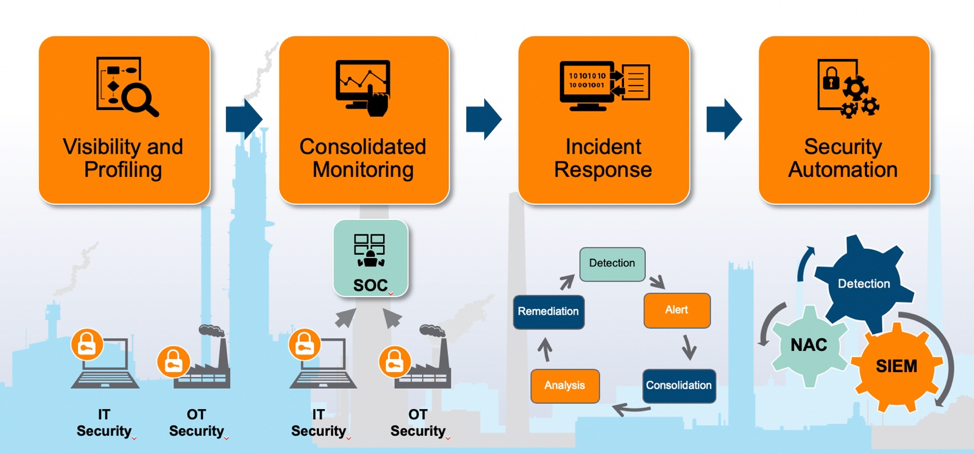
ICS Information Security Assurance Framework 15 - NSFOCUS, Inc., a global network and cyber security leader, protects enterprises and carriers from advanced cyber attacks.
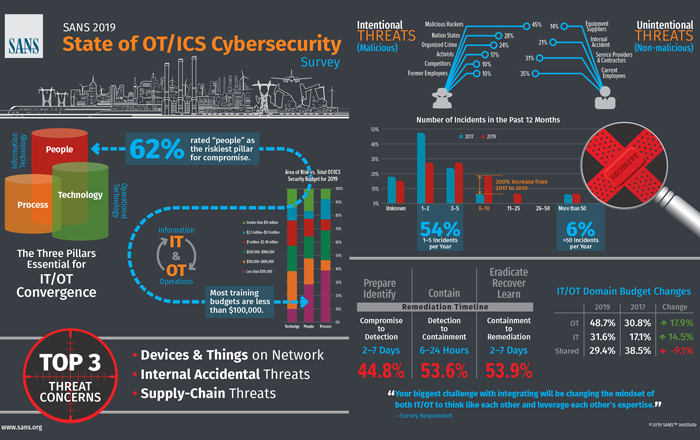
Industrial Control Systems Security Professionals Say Cyber Security Risk Is At Critical Levels, With People The Biggest Risk. - IT Security Guru